ECCouncil.312-50v12.v2023-01-09.q195
Exam Code: 312-50v12
Exam Name: Certified Ethical Hacker Exam
NEW QUESTION: 1
The configuration allows a wired or wireless network interface controller to pass all traffic it receives to the Central Processing Unit (CPU), rather than passing only the frames that the controller is intended to receive. Which of the following is being described?
A. Multi-cast mode
B. Port forwarding
C. WEM
D. Promiscuous mode
Answer:
NEW QUESTION: 2
You went to great lengths to install all the necessary technologies to prevent hacking attacks,
such as expensive firewalls, antivirus software, anti-spam systems and intrusion
detection/prevention tools in your company's network. You have configured the most secure
policies and tightened every device on your network. You are confident that hackers will never be
able to gain access to your network with complex security system in place.
Your peer, Peter Smith who works at the same department disagrees with you.
He says even the best network security technologies cannot prevent hackers gaining access to
the network because of presence of "weakest link" in the security chain.
What is Peter Smith talking about?
A. Untrained staff or ignorant computer users who inadvertently become the weakest link in your
security chain
B. "Polymorphic viruses" are the weakest link in the security chain since the Anti-Virus scanners
will not be able to detect these attacks
C. Continuous Spam e-mails cannot be blocked by your security system since spammers use
different techniques to bypass the filters in your gateway
D. "zero-day" exploits are the weakest link in the security chain since the IDS will not be able to
detect these attacks
Answer: (SHOW ANSWER)
NEW QUESTION: 3
what is the port to block first in case you are suspicious that an loT device has been
compromised?
A. 22
B. 443
C. 48101
D. 80
Answer: C (LEAVE A REPLY)
NEW QUESTION: 4
Emily, an extrovert obsessed with social media, posts a large amount of private information,
photographs, and location tags of recently visited places. Realizing this. James, a professional
hacker, targets Emily and her acquaintances, conducts a location search to detect their
geolocation by using an automated tool, and gathers information to perform other sophisticated
attacks. What is the tool employed by James in the above scenario?
A. ophcrack
B. Hootsuite
C. VisualRoute
D. HULK
Answer: (SHOW ANSWER)
Hootsuite may be a social media management platform that covers virtually each side of a social
media manager's role.
With only one platform users area unit ready to do the easy stuff like reverend cool content and
schedule posts on social media in all the high to managing team members and measure ROI.
There area unit many totally different plans to decide on from, from one user set up up to a
bespoken enterprise account that's appropriate for much larger organizations.
Conducting location search on social media sites such as Twitter, Instagram, and Facebook helps
attackers to detect the geolocation of the target. This information further helps attackers to
perform various social engineering and non-technical attacks. Many online tools such as
Followerwonk, Hootsuite, and Sysomos are available to search for both geotagged and nongeotagged
information on social media sites. Attackers search social media sites using these
online tools using keywords, usernames, date, time, and so on...
NEW QUESTION: 5
What is the most common method to exploit the "Bash Bug" or "Shellshock" vulnerability?
A. Manipulate format strings in text fields
B. SYN Flood
C. Through Web servers utilizing CGI (Common Gateway Interface) to send a malformed
environment variable to a vulnerable Web server
D. SSH
Answer: (SHOW ANSWER)
NEW QUESTION: 6
What is the following command used for?
net use \targetipc$ "" /u:""
A. Enumeration of Cisco routers
B. Grabbing the SAM
C. Grabbing the etc/passwd file
D. Connecting to a Linux computer through Samba.
E. This command is used to connect as a null session
Answer: (SHOW ANSWER)
NEW QUESTION: 7
To create a botnet. the attacker can use several techniques to scan vulnerable machines. The
attacker first collects Information about a large number of vulnerable machines to create a list.
Subsequently, they infect the machines. The list Is divided by assigning half of the list to the
newly compromised machines. The scanning process runs simultaneously. This technique
ensures the spreading and installation of malicious code in little time.
Which technique is discussed here?
A. Hit-list-scanning technique
B. Topological scanning technique
C. Subnet scanning technique
D. Permutation scanning technique
Answer: (SHOW ANSWER)
One of the biggest problems a worm faces in achieving a very fast rate of infection is "getting off
the ground." although a worm spreads exponentially throughout the early stages of infection, the
time needed to infect say the first 10,000 hosts dominates the infection time.
There is a straightforward way for an active worm a simple this obstacle, that we term hit-list
scanning. Before the worm is free, the worm author collects a listing of say ten,000 to 50,000
potentially vulnerable machines, ideally ones with sensible network connections. The worm, when
released onto an initial machine on this hit-list, begins scanning down the list. once it infects a
machine, it divides the hit-list in half, communicating half to the recipient worm, keeping the other
half.
This fast division ensures that even if only 10-20% of the machines on the hit-list are actually
vulnerable, an active worm can quickly bear the hit-list and establish itself on all vulnerable
machines in only some seconds. though the hit-list could begin at 200 kilobytes, it quickly shrinks
to nothing during the partitioning. This provides a great benefit in constructing a quick worm by
speeding the initial infection.
The hit-list needn't be perfect: a simple list of machines running a selected server sort could
serve, though larger accuracy can improve the unfold. The hit-list itself is generated victimization
one or many of the following techniques, ready well before, typically with very little concern of
detection.
Stealthy scans. Portscans are so common and then wide ignored that even a quick scan of the
whole net would be unlikely to attract law enforcement attention or over gentle comment within
the incident response community. However, for attackers wish to be particularly careful, a
randomised sneaky scan taking many months would be not possible to attract much attention, as
most intrusion detection systems are not currently capable of detecting such low-profile scans.
Some portion of the scan would be out of date by the time it had been used, however abundant of
it'd not.
Distributed scanning. an assailant might scan the web using a few dozen to some thousand
already-compromised "zombies," the same as what DDOS attackers assemble in a very fairly
routine fashion. Such distributed scanning has already been seen within the wild-Lawrence
Berkeley National Laboratory received ten throughout the past year.
DNS searches. Assemble a list of domains (for example, by using wide offered spam mail lists, or
trolling the address registries). The DNS will then be searched for the science addresses of mailservers
(via mx records) or net servers (by looking for www.domain.com).
Spiders. For net server worms (like Code Red), use Web-crawling techniques the same as search
engines so as to produce a list of most Internet-connected web sites. this would be unlikely to
draw in serious attention.
Public surveys. for many potential targets there may be surveys available listing them, like the
Netcraft survey.
Just listen. Some applications, like peer-to-peer networks, wind up advertising many of their
servers. Similarly, many previous worms effectively broadcast that the infected machine is
vulnerable to further attack. easy, because of its widespread scanning, during the Code Red I
infection it was easy to select up the addresses of upwards of 300,000 vulnerable IIS serversbecause
each came knock on everyone's door!
NEW QUESTION: 8
in this form of encryption algorithm, every Individual block contains 64-bit data, and three keys are
used, where each key consists of 56 bits. Which is this encryption algorithm?
A. IDEA
B. Triple Data Encryption standard
C. MDS encryption algorithm
D. AES
Answer: (SHOW ANSWER)
Triple DES is another mode of DES operation. It takes three 64-bit keys, for an overall key length
of 192 bits. In Stealth, you merely type within the entire 192-bit (24 character) key instead of
entering each of the three keys individually. The Triple DES DLL then breaks the user-provided
key into three subkeys, padding the keys if necessary in order that they are each 64 bits long.
The procedure for encryption is strictly an equivalent as regular DES, but it's repeated 3 times ,
hence the name Triple DES. the info is encrypted with the primary key, decrypted with the second
key, and eventually encrypted again with the third key. Triple DES runs 3 times slower than DES,
but is far safer if used properly. The procedure for decrypting something is that the same because
the procedure for encryption, except it's executed in reverse. Like DES, data is encrypted and
decrypted in 64-bit chunks. Although the input key for DES is 64 bits long, the particular key
employed by DES is merely 56 bits long . the smallest amount significant (right-most) bit in each
byte may be a parity , and will be set in order that there are always an odd number of 1s in every
byte. These parity bits are ignored, so only the seven most vital bits of every byte are used,
leading to a key length of 56 bits. this suggests that the effective key strength for Triple DES is
really 168 bits because each of the three keys contains 8 parity bits that aren't used during the
encryption process. Triple DES Modes Triple ECB (Electronic Code Book) * This variant of Triple
DES works precisely the same way because the ECB mode of DES. * this is often the foremost
commonly used mode of operation. Triple CBC (Cipher Block Chaining) * This method is
extremely almost like the quality DES CBC mode. * like Triple ECB, the effective key length is 168
bits and keys are utilized in an equivalent manner, as described above, but the chaining features
of CBC mode also are employed. * the primary 64-bit key acts because the Initialization Vector to
DES. * Triple ECB is then executed for one 64-bit block of plaintext. * The resulting ciphertext is
then XORed with subsequent plaintext block to be encrypted, and therefore the procedure is
repeated. * This method adds an additional layer of security to Triple DES and is therefore safer
than Triple ECB, although it's not used as widely as Triple ECB.
NEW QUESTION: 9
Shiela is an information security analyst working at HiTech Security Solutions. She is performing
service version discovery using Nmap to obtain information about the running services and their
versions on a target system.
Which of the following Nmap options must she use to perform service version discovery on the
target host?
A. -SX
B. -SN
C. -sV
D. -SF
Answer: (SHOW ANSWER)
NEW QUESTION: 10
A. You should use netstat to check for any suspicious connections with another IP address within
the LAN.
B. You should check your ARP table and see if there is one IP address with two different MAC
addresses.
C. You should scan the network using Nmap to check the MAC addresses of all the hosts and
look for duplicates.
D. You cannot identify such an attack and must use a VPN to protect your traffic, r
Answer: (SHOW ANSWER)
NEW QUESTION: 11
The network administrator at Spears Technology, Inc has configured the default gateway Cisco
router's access-list as below:
You are hired to conduct security testing on their network.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list configured at the router prevents you from establishing a successful connection.
You want to retrieve the Cisco configuration from the router. How would you proceed?
A. Use the Cisco's TFTP default password to connect and download the configuration file
B. Run a network sniffer and capture the returned traffic with the configuration file from the router
C. Run Generic Routing Encapsulation (GRE) tunneling protocol from your computer to the router
masking your IP address
D. Send a customized SNMP set request with a spoofed source IP address in the range
-192.168.1.0
Answer: (SHOW ANSWER)
NEW QUESTION: 12
The Payment Card Industry Data Security Standard (PCI DSS) contains six different categories of
control objectives. Each objective contains one or more requirements, which must be followed in
order to achieve compliance. Which of the following requirements would best fit under the
objective, "Implement strong access control measures"?
A. Regularly test security systems and processes.
B. Assign a unique ID to each person with computer access.
C. Use and regularly update anti-virus software on all systems commonly affected by malware.
D. Encrypt transmission of cardholder data across open, public networks.
Answer: (SHOW ANSWER)
NEW QUESTION: 13
Windows LAN Manager (LM) hashes are known to be weak.
Which of the following are known weaknesses of LM? (Choose three.)
A. Makes use of only 32-bit encryption.
B. Hashes are sent in clear text over the network.
C. Effective length is 7 characters.
D. Converts passwords to uppercase.
Answer: (SHOW ANSWER)
NEW QUESTION: 14
Steve, a scientist who works in a governmental security agency, developed a technological
solution to identify people based on walking patterns and implemented this approach to a physical
control access.
A camera captures people walking and identifies the individuals using Steve's approach.
After that, people must approximate their RFID badges. Both the identifications are required to
open the door. In this case, we can say:
A. Although the approach has two phases, it actually implements just one authentication factor
B. Biological motion cannot be used to identify people
C. The solution implements the two authentication factors: physical object and physical
characteristic
D. The solution will have a high level of false positives
Answer: (SHOW ANSWER)
NEW QUESTION: 15
In the field of cryptanalysis, what is meant by a "rubber-hose" attack?
A. Forcing the targeted keystream through a hardware-accelerated device such as an ASIC.
B. A backdoor placed into a cryptographic algorithm by its creator.
C. Extraction of cryptographic secrets through coercion or torture.
D. Attempting to decrypt ciphertext by making logical assumptions about the contents of the
original plaintext.
Answer: (SHOW ANSWER)
A powerful and often the most effective cryptanalysis method in which the attack is directed at the
most vulnerable link in the cryptosystem - the person. In this attack, the cryptanalyst uses
blackmail, threats, torture, extortion, bribery, etc. This method's main advantage is the decryption
time's fundamental independence from the volume of secret information, the length of the key,
and the cipher's mathematical strength.
The method can reduce the time to guess a password, for example, for AES, to an acceptable
level; however, it requires special authorization from the relevant regulatory authorities.
Therefore, it is outside the scope of this course and is not considered in its practical part.
NEW QUESTION: 16
What would you enter if you wanted to perform a stealth scan using Nmap?
A. nmap -sT
B. nmap -sU
C. nmap -sS
D. nmap -sM
Answer: (SHOW ANSWER)
Valid 312-50v12 Dumps shared by PassTestKing.com for Helping Passing 312-50v12 Exam!
PassTestKing.com now offer the newest 312-50v12 exam dumps, the PassTestKing.com
312-50v12 exam questions have been updated and answers have been corrected get the
newest PassTestKing.com 312-50v12 dumps with Test Engine here:
https://www.passtestking.com/ECCouncil/312-50v12-practice-exam-dumps.html (505 Q&As
Dumps, 35%OFF Special Discount Code: freecram)
NEW QUESTION: 17
The Heartbleed bug was discovered in 2014 and is widely referred to under MITRE's Common
Vulnerabilities and Exposures (CVE) as CVE-2014-0160. This bug affects the OpenSSL
implementation of the Transport Layer Security (TLS) protocols defined in RFC6520.
What type of key does this bug leave exposed to the Internet making exploitation of any
compromised system very easy?
A. Public
B. Root
C. Shared
D. Private
Answer: (SHOW ANSWER)
NEW QUESTION: 18
When a normal TCP connection starts, a destination host receives a SYN (synchronize/start)
packet from a source host and sends back a SYN/ACK (synchronize acknowledge). The
destination host must then hear an ACK (acknowledge) of the SYN/ACK before the connection is
established. This is referred to as the "TCP three-way handshake." While waiting for the ACK to
the SYN ACK, a connection queue of finite size on the destination host keeps track of
connections waiting to be completed. This queue typically empties quickly since the ACK is
expected to arrive a few milliseconds after the SYN ACK.
How would an attacker exploit this design by launching TCP SYN attack?
A. Attacker generates TCP ACK packets with random source addresses towards a victim host
B. Attacker generates TCP RST packets with random source addresses towards a victim host
C. Attacker floods TCP SYN packets with random source addresses towards a victim host
D. Attacker generates TCP SYN packets with random destination addresses towards a victim
host
Answer: C (LEAVE A REPLY)
NEW QUESTION: 19
How does a denial-of-service attack work?
A. A hacker prevents a legitimate user (or group of users) from accessing a service
B. A hacker tries to decipher a password by using a system, which subsequently crashes the
network
C. A hacker attempts to imitate a legitimate user by confusing a computer or even another person
D. A hacker uses every character, word, or letter he or she can think of to defeat authentication
Answer: (SHOW ANSWER)
NEW QUESTION: 20
A. WHOIS
B. IETF
C. CAPTCHA
D. IANA
Answer: (SHOW ANSWER)
NEW QUESTION: 21
Which of the following are well known password-cracking programs?
A. Netbus
B. NetCat
C. John the Ripper
D. L0phtcrack
E. Jack the Ripper
Answer: (SHOW ANSWER)
NEW QUESTION: 22
Which of the following is not a Bluetooth attack?
A. Bluedriving
B. Bluesmacking
C. Bluejacking
D. Bluesnarfing
Answer: (SHOW ANSWER)

 github.com
github.com
Bluedriving is a bluetooth wardriving utility. It can capture bluetooth devices, lookup their services,
get GPS information and present everything in a nice web page. It can search for and show a lot
of information about the device, the GPS address and the historic location of devices on a map.
The main motivation of this tool is to research about the targeted surveillance of people by means
of its cellular phone or car. With this tool you can capture information about bluetooth devices and
show, on a map, the points where you have seen the same device in the past.
NEW QUESTION: 23
Which tool can be used to silently copy files from USB devices?
A. USB Snoopy
B. USB Sniffer
C. Use Dumper
D. USB Grabber
Answer: C (LEAVE A REPLY)
NEW QUESTION: 24
While using your bank's online servicing you notice the following string in the URL bar:
"http: // www. MyPersonalBank. com/ account?
id=368940911028389&Damount=10980&Camount=21" You observe that if you modify the
Damount & Camount values and submit the request, that data on the web page reflects the
changes.
Which type of vulnerability is present on this site?
A. XSS Reflection
B. Cookie Tampering
C. Web Parameter Tampering
D. SQL Injection
Answer: (SHOW ANSWER)
NEW QUESTION: 25
Peter, a system administrator working at a reputed IT firm, decided to work from his home and
login remotely. Later, he anticipated that the remote connection could be exposed to session
hijacking. To curb this possibility, he implemented a technique that creates a safe and encrypted
tunnel over a public network to securely send and receive sensitive information and prevent
hackers from decrypting the data flow between the endpoints. What is the technique followed by
Peter to send files securely through a remote connection?
A. SMB signing
B. VPN
C. DMZ
D. Switch network
Answer: (SHOW ANSWER)
NEW QUESTION: 26
Mirai malware targets loT devices. After infiltration, it uses them to propagate and create botnets
that then used to launch which types of attack?
A. Password attack
B. DDoS attack
C. MITM attack
D. Birthday attack
Answer: (SHOW ANSWER)
NEW QUESTION: 27
Todd has been asked by the security officer to purchase a counter-based authentication system.
Which of the following best describes this type of system?
A. An authentication system that creates one-time passwords that are encrypted with secret keys.
B. An authentication system that uses passphrases that are converted into virtual passwords.
C. A biometric system that bases authentication decisions on behavioral attributes.
D. A biometric system that bases authentication decisions on physical attributes.
Answer: (SHOW ANSWER)
NEW QUESTION: 28
Shellshock allowed an unauthorized user to gain access to a server. It affected many Internetfacing
services, which OS did it not directly affect?
A. Linux
B. Unix
C. Windows
D. OS X
Answer: (SHOW ANSWER)
NEW QUESTION: 29
Calvin, a software developer, uses a feature that helps him auto-generate the content of a web
page without manual involvement and is integrated with SSI directives. This leads to a
vulnerability in the developed web application as this feature accepts remote user inputs and uses
them on the page. Hackers can exploit this feature and pass malicious SSI directives as input
values to perform malicious activities such as modifying and erasing server files. What is the type
of injection attack Calvin's web application is susceptible to?
A. CRLF injection
B. Server-side JS injection
C. Server-side includes injection
D. Server-side template injection
Answer: (SHOW ANSWER)
NEW QUESTION: 30
A. Brute Force Attack
B. Online Attack
C. Dictionary Attack
D. Hybrid Attack
Answer: (SHOW ANSWER)
NEW QUESTION: 31
Although FTP traffic is not encrypted by default, which layer 3 protocol would allow for end-to-end
encryption of the connection?
A. SFTP
B. Ipsec
C. SSL
D. FTPS
Answer: (SHOW ANSWER)
 en.wikipedia.org
en.wikipedia.org
Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and
encrypts the packets of data to provide secure encrypted communication between two computers
over an Internet Protocol network. It is used in virtual private networks (VPNs).
IPsec includes protocols for establishing mutual authentication between agents at the beginning
of a session and negotiation of cryptographic keys to use during the session. IPsec can protect
data flows between a pair of hosts (host-to-host), between a pair of security gateways (networkto-
network), or between a security gateway and a host (network-to-host). IPsec uses
cryptographic security services to protect communications over Internet Protocol (IP) networks. It
supports network-level peer authentication, data-origin authentication, data integrity, data
confidentiality (encryption), and replay protection.
The initial IPv4 suite was developed with few security provisions. As a part of the IPv4
enhancement, IPsec is a layer 3 OSI model or internet layer end-to-end security scheme. In
contrast, while some other Internet security systems in widespread use operate above layer 3,
such as Transport Layer Security (TLS) that operates at the Transport Layer and Secure Shell
(SSH) that operates at the Application layer, IPsec can automatically secure applications at the IP
layer.
Incorrect answers:
SFTP https://en.wikipedia.org/wiki/File_Transfer_Protocol#FTP_over_SSH
FTP over SSH is the practice of tunneling a normal FTP session over a Secure Shell connection.
[27] Because FTP uses multiple TCP connections (unusual for a TCP/IP protocol that is still in
use), it is particularly difficult to tunnel over SSH. With many SSH clients, attempting to set up a
tunnel for the control channel (the initial client-to-server connection on port 21) will protect only
that channel; when data is transferred, the FTP software at either end sets up new TCP
connections (data channels) and thus have no confidentiality or integrity protection.
FTPS https://en.wikipedia.org/wiki/FTPS
FTPS (also known FTP-SSL, and FTP Secure) is an extension to the commonly used File
Transfer Protocol (FTP) that adds support for the Transport Layer Security (TLS) and, formerly,
the Secure Sockets Layer cryptographic protocols.
SSL https://en.wikipedia.org/wiki/Transport_Layer_Security
Transport Layer Security (TLS), and its now-deprecated predecessor, Secure Sockets Layer
(SSL), are cryptographic protocols designed to provide communications security over a computer
network. Several versions of the protocols are widely used in applications such as web browsing,
email, instant messaging, and voice over IP (VoIP). Websites can use TLS to secure all
communications between their servers and web browsers.
NOTE: All of these protocols are the application layer of the OSI model.
Valid 312-50v12 Dumps shared by PassTestKing.com for Helping Passing 312-50v12 Exam!
PassTestKing.com now offer the newest 312-50v12 exam dumps, the PassTestKing.com
312-50v12 exam questions have been updated and answers have been corrected get the
newest PassTestKing.com 312-50v12 dumps with Test Engine here:
https://www.passtestking.com/ECCouncil/312-50v12-practice-exam-dumps.html (505 Q&As
Dumps, 35%OFF Special Discount Code: freecram)
NEW QUESTION: 32
which of the following Bluetooth hacking techniques refers to the theft of information from a
wireless device through Bluetooth?
A. Bluesmacking
B. Bluebugging
C. Bluejacking
D. Bluesnarfing
Answer: (SHOW ANSWER)
Bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth
connection, often between phones, desktops, laptops, and PDAs (personal digital assistant).
NEW QUESTION: 33
A zone file consists of which of the following Resource Records (RRs)?
A. SOA, NS, A, and MX records
B. SOA, NS, AXFR, and MX records
C. DNS, NS, PTR, and MX records
D. DNS, NS, AXFR, and MX records
Answer: (SHOW ANSWER)
NEW QUESTION: 34
Which of the following commands checks for valid users on an SMTP server?
A. RCPT
B. CHK
C. VRFY
D. EXPN
Answer: C (LEAVE A REPLY)
The VRFY commands enables SMTP clients to send an invitation to an SMTP server to verify
that mail for a selected user name resides on the server. The VRFY command is defined in RFC
821. The server sends a response indicating whether the user is local or not, whether mail are
going to be forwarded, and so on. A response of 250 indicates that the user name is local; a
response of 251 indicates that the user name isn't local, but the server can forward the message.
The server response includes the mailbox name.
NEW QUESTION: 35
Which iOS jailbreaking technique patches the kernel during the device boot so that it becomes
jailbroken after each successive reboot?
A. Tethered jailbreaking
B. Semi-tethered jailbreaking
C. Untethered jailbreaking
D. Semi-Untethered jailbreaking
Answer: (SHOW ANSWER)
An untethered jailbreak is one that allows a telephone to finish a boot cycle when being pwned
with none interruption to jailbreak-oriented practicality.
Untethered jailbreaks area unit the foremost sought-after of all, however they're additionally the
foremost difficult to attain due to the powerful exploits and organic process talent they need.
associate unbound jailbreak is sent over a physical USB cable association to a laptop or directly
on the device itself by approach of associate application-based exploit, like a web site in
campaign.
Upon running associate unbound jailbreak, you'll be able to flip your pwned telephone off and on
once more while not running the jailbreak tool once more. all of your jailbreak tweaks and apps
would then continue in operation with none user intervention necessary.
It's been an extended time since IOS has gotten the unbound jailbreak treatment. the foremost
recent example was the computer-based Pangu break, that supported most handsets that ran
IOS nine.1. We've additionally witnessed associate unbound jailbreak within the kind of
JailbreakMe, that allowed users to pwn their handsets directly from the mobile campaign
applications programme while not a laptop.
NEW QUESTION: 36
A newly joined employee. Janet, has been allocated an existing system used by a previous
employee. Before issuing the system to Janet, it was assessed by Martin, the administrator.
Martin found that there were possibilities of compromise through user directories, registries, and
other system parameters. He also Identified vulnerabilities such as native configuration tables,
incorrect registry or file permissions, and software configuration errors. What is the type of
vulnerability assessment performed by Martin?
A. Credentialed assessment
B. Database assessment
C. Host-based assessment
D. Distributed assessment
Answer: (SHOW ANSWER)
The host-based vulnerability assessment (VA) resolution arose from the auditors' got to
periodically review systems. Arising before the net becoming common, these tools typically take
an "administrator's eye" read of the setting by evaluating all of the knowledge that an
administrator has at his or her disposal.
Uses
Host VA tools verify system configuration, user directories, file systems, registry settings, and all
forms of other info on a number to gain information about it. Then, it evaluates the chance of
compromise. it should also live compliance to a predefined company policy so as to satisfy an
annual audit. With administrator access, the scans area unit less possible to disrupt traditional
operations since the computer code has the access it has to see into the complete configuration
of the system.
What it Measures Host
VA tools will examine the native configuration tables and registries to spot not solely apparent
vulnerabilities, however additionally "dormant" vulnerabilities - those weak or misconfigured
systems and settings which will be exploited when an initial entry into the setting. Host VA
solutions will assess the safety settings of a user account table; the access management lists
related to sensitive files or data; and specific levels of trust applied to other systems. The host VA
resolution will a lot of accurately verify the extent of the danger by determinant however way any
specific exploit could also be ready to get.
NEW QUESTION: 37
Andrew is an Ethical Hacker who was assigned the task of discovering all the active devices
hidden by a restrictive firewall in the IPv4 range in a given target network.
Which of the following host discovery techniques must he use to perform the given task?
A. UDP scan
B. TCP Maimon scan
C. arp ping scan
D. ACK flag probe scan
Answer: (SHOW ANSWER)
One of the most common Nmap usage scenarios is scanning an Ethernet LAN. Most LANs,
especially those that use the private address range granted by RFC 1918, do not always use the
overwhelming majority of IP addresses. When Nmap attempts to send a raw IP packet, such as
an ICMP echo request, the OS must determine a destination hardware (ARP) address, such as
the target IP, so that the Ethernet frame can be properly addressed. .. This is required to issue a
series of ARP requests. This is best illustrated by an example where a ping scan is attempted
against an Area Ethernet host. The -send-ip option tells Nmap to send IP-level packets (rather
than raw Ethernet), even on area networks. The Wireshark output of the three ARP requests and
their timing have been pasted into the session.
Raw IP ping scan example for offline targets
This example took quite a couple of seconds to finish because the (Linux) OS sent three ARP
requests at 1 second intervals before abandoning the host. Waiting for a few seconds is
excessive, as long as the ARP response usually arrives within a few milliseconds. Reducing this
timeout period is not a priority for OS vendors, as the overwhelming majority of packets are sent
to the host that actually exists. Nmap, on the other hand, needs to send packets to 16 million IP s
given a target like 10.0.0.0/8. Many targets are pinged in parallel, but waiting 2 seconds each is
very delayed.
There is another problem with raw IP ping scans on the LAN. If the destination host turns out to
be unresponsive, as in the previous example, the source host usually adds an incomplete entry
for that destination IP to the kernel ARP table. ARP tablespaces are finite and some operating
systems become unresponsive when full. If Nmap is used in rawIP mode (-send-ip), Nmap may
have to wait a few minutes for the ARP cache entry to expire before continuing host discovery.
ARP scans solve both problems by giving Nmap the highest priority. Nmap issues raw ARP
requests and handles retransmissions and timeout periods in its sole discretion. The system ARP
cache is bypassed. The example shows the difference. This ARP scan takes just over a tenth of
the time it takes for an equivalent IP.
Example b ARP ping scan of offline target
In example b, neither the -PR option nor the -send-eth option has any effect. This is often
because ARP has a default scan type on the Area Ethernet network when scanning Ethernet
hosts that Nmap discovers. This includes traditional wired Ethernet as 802.11 wireless networks.
As mentioned above, ARP scanning is not only more efficient, but also more accurate. Hosts
frequently block IP-based ping packets, but usually cannot block ARP requests or responses and
communicate over the network.Nmap uses ARP instead of all targets on equivalent targets, even
if different ping types (such as -PE and -PS) are specified. LAN.. If you do not need to attempt an
ARP scan at all, specify -send-ip as shown in Example a "Raw IP Ping Scan for Offline Targets".
If you give Nmap control to send raw Ethernet frames, Nmap can also adjust the source MAC
address. If you have the only PowerBook in your security conference room and a large ARP scan
is initiated from an Apple-registered MAC address, your head may turn to you. Use the -spoofmac
option to spoof the MAC address as described in the MAC Address Spoofing section.
NEW QUESTION: 38
What port number is used by LDAP protocol?
A. 445
B. 110
C. 389
D. 464
Answer: (SHOW ANSWER)
NEW QUESTION: 39
Matthew, a black hat, has managed to open a meterpreter session to one of the kiosk machines
in Evil Corp's lobby. He checks his current SID, which is
S-1-5-21-1223352397-1872883824-861252104-501. What needs to happen before Matthew has
full administrator access?
A. He already has admin privileges, as shown by the "501" at the end of the SID.
B. He needs to gain physical access.
C. He needs to disable antivirus protection.
D. He must perform privilege escalation.
Answer: (SHOW ANSWER)
NEW QUESTION: 40
A. SYN
B. RST
C. ACK
D. No return response
Answer: (SHOW ANSWER)
NEW QUESTION: 41
Sam is a penetration tester hired by Inception Tech, a security organization. He was asked to
perform port scanning on a target host in the network. While performing the given task, Sam
sends FIN/ACK probes and determines that an RST packet is sent in response by the target host,
indicating that the port is closed.
What is the port scanning technique used by Sam to discover open ports?
A. Xmas scan
B. IDLE/IPID header scan
C. TCP Maimon scan
D. ACK flag probe scan
Answer: (SHOW ANSWER)
TCP Maimon scan
This scan technique is very similar to NULL, FIN, and Xmas scan, but the probe used here is
FIN/ACK. In most cases, to determine if the port is open or closed, the RST packet should be
generated as a response to a probe request. However, in many BSD systems, the port is open if
the packet gets dropped in response to a probe.
How Nmap interprets responses to a Maimon scan probe
Probe Response Assigned State
No response received (even after retransmissions) open|filtered
TCP RST packet closed
ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) filtered
NEW QUESTION: 42
which of the following information security controls creates an appealing isolated environment for
hackers to prevent them from compromising critical targets while simultaneously gathering
information about the hacker?
A. intrusion detection system
B. Honeypot
C. Botnet
Answer: (SHOW ANSWER)
D Firewall
Explanation:
A honeypot may be a trap that an IT pro lays for a malicious hacker, hoping that they will interact
with it during a way that gives useful intelligence. It's one among the oldest security measures in
IT, but beware: luring hackers onto your network, even on an isolated system, are often a
dangerous game. honeypot may be a good starting place: "A honeypot may be a computer or
computing system intended to mimic likely targets of cyberattacks." Often a honeypot are going to
be deliberately configured with known vulnerabilities in situation to form a more tempting or
obvious target for attackers. A honeypot won't contain production data or participate in legitimate
traffic on your network - that's how you'll tell anything happening within it's a results of an attack. If
someone's stopping by, they're up to no good. That definition covers a various array of systems,
from bare-bones virtual machines that only offer a couple of vulnerable systems to ornately
constructed fake networks spanning multiple servers. and therefore the goals of these who build
honeypots can vary widely also , starting from defense thorough to academic research.
additionally , there's now an entire marketing category of deception technology that, while not
meeting the strict definition of a honeypot, is certainly within the same family. But we'll get thereto
during a moment. honeypots aim to permit close analysis of how hackers do their dirty work. The
team controlling the honeypot can watch the techniques hackers use to infiltrate systems,
escalate privileges, and otherwise run amok through target networks. These sorts of honeypots
are found out by security companies, academics, and government agencies looking to look at the
threat landscape. Their creators could also be curious about learning what kind of attacks are out
there, getting details on how specific sorts of attacks work, or maybe trying to lure a specific
hackers within the hopes of tracing the attack back to its source. These systems are often inbuilt
fully isolated lab environments, which ensures that any breaches don't end in non-honeypot
machines falling prey to attacks. Production honeypots, on the opposite hand, are usually
deployed in proximity to some organization's production infrastructure, though measures are
taken to isolate it the maximum amount as possible. These honeypots often serve both as bait to
distract hackers who could also be trying to interrupt into that organization's network, keeping
them faraway from valuable data or services; they will also function a canary within the coalpit ,
indicating that attacks are underway and are a minimum of partially succeeding.
NEW QUESTION: 43
Roma is a member of a security team. She was tasked with protecting the internal network of an
organization from imminent threats. To accomplish this task, Roma fed threat intelligence into the
security devices in a digital format to block and identify inbound and outbound malicious traffic
entering the organization's network.
Which type of threat intelligence is used by Roma to secure the internal network?
A. Strategic threat intelligence
B. Tactical threat intelligence
C. Operational threat intelligence
D. Technical threat intelligence
Answer: (SHOW ANSWER)
NEW QUESTION: 44
John wants to send Marie an email that includes sensitive information, and he does not trust the
network that he is connected to. Marie gives him the idea of using PGP. What should John do to
communicate correctly using this type of encryption?
A. Use his own public key to encrypt the message.
B. Use Marie's public key to encrypt the message.
C. Use his own private key to encrypt the message.
D. Use Marie's private key to encrypt the message.
Answer: B (LEAVE A REPLY)
When a user encrypts plaintext with PGP, PGP first compresses the plaintext. The session key
works with a very secure, fast conventional encryption algorithm to encrypt the plaintext; the
result is ciphertext. Once the data is encrypted, the session key is then encrypted to the
recipient's public key
 en.wikipedia.org
en.wikipedia.org
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and
authentication for data communication. PGP is used for signing, encrypting, and decrypting texts,
e-mails, files, directories, and whole disk partitions and to increase the security of e-mail
communications.
PGP encryption uses a serial combination of hashing, data compression, symmetric-key
cryptography, and finally public-key cryptography; each step uses one of several supported
algorithms. Each public key is bound to a username or an e-mail address.
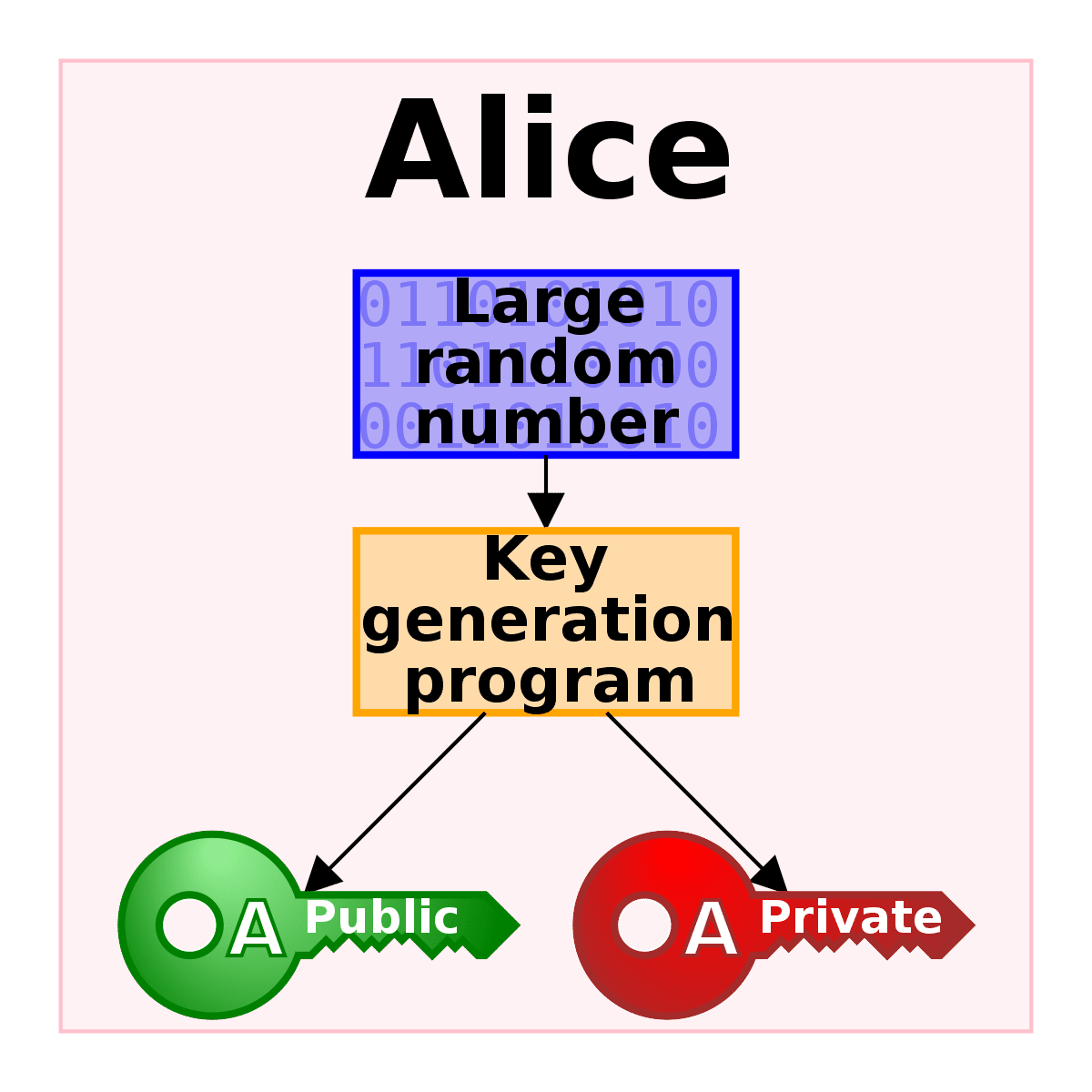
 en.wikipedia.org
en.wikipedia.org
Public key encryption uses two different keys. One key is used to encrypt the information and the
other is used to decrypt the information. Sometimes this is referred to as asymmetric encryption
because two keys are required to make the system and/or process work securely. One key is
known as the public key and should be shared by the owner with anyone who will be securely
communicating with the key owner. However, the owner's secret key is not to be shared and
considered a private key. If the private key is shared with unauthorized recipients, the encryption
mechanisms protecting the information must be considered compromised.
NEW QUESTION: 45
Sam, a web developer, was instructed to incorporate a hybrid encryption software program into a
web application to secure email messages. Sam used an encryption software, which is a free
implementation of the OpenPGP standard that uses both symmetric-key cryptography and
asymmetric-key cryptography for improved speed and secure key exchange. What is the
encryption software employed by Sam for securing the email messages?
A. GPG
B. SMTP
C. PGP
D. S/MIME
Answer: C (LEAVE A REPLY)
NEW QUESTION: 46
Which of the following is considered an exploit framework and has the ability to perform
automated attacks on services, ports, applications and unpatched security flaws in a computer
system?
A. Wireshark
B. Maltego
C. Metasploit
D. Nessus
Answer: (SHOW ANSWER)
 en.wikipedia.org
en.wikipedia.org
The Metasploit Project is a computer security project that provides information about security
vulnerabilities and aids in penetration testing and IDS signature development. It is owned by
Boston, Massachusetts-based security company Rapid7.
Its best-known sub-project is the open-source Metasploit Framework, a tool for developing and
executing exploit code against a remote target machine. Other important sub-projects include the
Opcode Database, shellcode archive and related research.
The Metasploit Project includes anti-forensic and evasion tools, some of which are built into the
Metasploit Framework. Metasploit is pre-installed in the Kali Linux operating system.
The basic steps for exploiting a system using the Framework include.
1. Optionally checking whether the intended target system is vulnerable to an exploit.
2. Choosing and configuring an exploit (code that enters a target system by taking advantage of
one of its bugs; about 900 different exploits for Windows, Unix/Linux and macOS systems are
included).
3. Choosing and configuring a payload (code that will be executed on the target system upon
successful entry; for instance, a remote shell or a VNC server). Metasploit often recommends a
payload that should work.
4. Choosing the encoding technique so that hexadecimal opcodes known as "bad characters" are
removed from the payload, these characters will cause the exploit to fail.
5. Executing the exploit.
This modular approach - allowing the combination of any exploit with any payload - is the major
advantage of the Framework. It facilitates the tasks of attackers, exploit writers and payload
writers.
Valid 312-50v12 Dumps shared by PassTestKing.com for Helping Passing 312-50v12 Exam!
PassTestKing.com now offer the newest 312-50v12 exam dumps, the PassTestKing.com
312-50v12 exam questions have been updated and answers have been corrected get the
newest PassTestKing.com 312-50v12 dumps with Test Engine here:
https://www.passtestking.com/ECCouncil/312-50v12-practice-exam-dumps.html (505 Q&As
Dumps, 35%OFF Special Discount Code: freecram)
NEW QUESTION: 47
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that
allows session oriented connections (Telnet) and performs the sequence prediction on the target
operating system. He manages to find an active session due to the high level of traffic on the
network. What is Bob supposed to do next?
A. Guess the sequence numbers
B. Reverse sequence prediction
C. Take over the session
D. Take one of the parties offline
Answer: (SHOW ANSWER)
NEW QUESTION: 48
An attacker runs netcat tool to transfer a secret file between two hosts.
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
A. Use cryptcat instead of netcat
B. Machine A: netcat -l -p 1234 < testfile -pw passwordMachine B: netcat <machine A IP> 1234 -
pw password
C. Machine A: netcat -l -e magickey -p 1234 < testfileMachine B: netcat <machine A IP> 1234
D. Machine A: netcat -l -p -s password 1234 < testfileMachine B: netcat <machine A IP> 1234
Answer: (SHOW ANSWER)
NEW QUESTION: 49
Based on the below log, which of the following sentences are true?
Mar 1, 2016, 7:33:28 AM 10.240.250.23 - 54373 10.249.253.15 - 22 tcp_ip
A. Application is FTP and 10.240.250.23 is the client and 10.249.253.15 is the server.
B. Application is SSH and 10.240.250.23 is the server and 10.249.253.15 is the client.
C. SSH communications are encrypted; it's impossible to know who is the client or the server.
D. Application is SSH and 10.240.250.23 is the client and 10.249.253.15 is the server.
Answer: (SHOW ANSWER)
Mar 1, 2016, 7:33:28 AM 10.240.250.23 - 54373 10.249.253.15 - 22 tcp_ip Let's just disassemble
this entry.
Mar 1, 2016, 7:33:28 AM - time of the request
10.240.250.23 - 54373 - client's IP and port
10.249.253.15 - server IP
- 22 - SSH port
NEW QUESTION: 50
A. sudo tshark -f''net 192 .68.8.0/24''
B. wireshark --capture --local masked 192.168.8.0 ---range 24
C. tshark -net 192.255.255.255 mask 192.168.8.0
D. wireshark --fetch ''192.168.8*''
Answer: (SHOW ANSWER)
Exam Code: 312-50v12
Exam Name: Certified Ethical Hacker Exam
NEW QUESTION: 1
The configuration allows a wired or wireless network interface controller to pass all traffic it receives to the Central Processing Unit (CPU), rather than passing only the frames that the controller is intended to receive. Which of the following is being described?
A. Multi-cast mode
B. Port forwarding
C. WEM
D. Promiscuous mode
Answer:
NEW QUESTION: 2
You went to great lengths to install all the necessary technologies to prevent hacking attacks,
such as expensive firewalls, antivirus software, anti-spam systems and intrusion
detection/prevention tools in your company's network. You have configured the most secure
policies and tightened every device on your network. You are confident that hackers will never be
able to gain access to your network with complex security system in place.
Your peer, Peter Smith who works at the same department disagrees with you.
He says even the best network security technologies cannot prevent hackers gaining access to
the network because of presence of "weakest link" in the security chain.
What is Peter Smith talking about?
A. Untrained staff or ignorant computer users who inadvertently become the weakest link in your
security chain
B. "Polymorphic viruses" are the weakest link in the security chain since the Anti-Virus scanners
will not be able to detect these attacks
C. Continuous Spam e-mails cannot be blocked by your security system since spammers use
different techniques to bypass the filters in your gateway
D. "zero-day" exploits are the weakest link in the security chain since the IDS will not be able to
detect these attacks
Answer: (SHOW ANSWER)
NEW QUESTION: 3
what is the port to block first in case you are suspicious that an loT device has been
compromised?
A. 22
B. 443
C. 48101
D. 80
Answer: C (LEAVE A REPLY)
NEW QUESTION: 4
Emily, an extrovert obsessed with social media, posts a large amount of private information,
photographs, and location tags of recently visited places. Realizing this. James, a professional
hacker, targets Emily and her acquaintances, conducts a location search to detect their
geolocation by using an automated tool, and gathers information to perform other sophisticated
attacks. What is the tool employed by James in the above scenario?
A. ophcrack
B. Hootsuite
C. VisualRoute
D. HULK
Answer: (SHOW ANSWER)
Hootsuite may be a social media management platform that covers virtually each side of a social
media manager's role.
With only one platform users area unit ready to do the easy stuff like reverend cool content and
schedule posts on social media in all the high to managing team members and measure ROI.
There area unit many totally different plans to decide on from, from one user set up up to a
bespoken enterprise account that's appropriate for much larger organizations.
Conducting location search on social media sites such as Twitter, Instagram, and Facebook helps
attackers to detect the geolocation of the target. This information further helps attackers to
perform various social engineering and non-technical attacks. Many online tools such as
Followerwonk, Hootsuite, and Sysomos are available to search for both geotagged and nongeotagged
information on social media sites. Attackers search social media sites using these
online tools using keywords, usernames, date, time, and so on...
NEW QUESTION: 5
What is the most common method to exploit the "Bash Bug" or "Shellshock" vulnerability?
A. Manipulate format strings in text fields
B. SYN Flood
C. Through Web servers utilizing CGI (Common Gateway Interface) to send a malformed
environment variable to a vulnerable Web server
D. SSH
Answer: (SHOW ANSWER)
NEW QUESTION: 6
What is the following command used for?
net use \targetipc$ "" /u:""
A. Enumeration of Cisco routers
B. Grabbing the SAM
C. Grabbing the etc/passwd file
D. Connecting to a Linux computer through Samba.
E. This command is used to connect as a null session
Answer: (SHOW ANSWER)
NEW QUESTION: 7
To create a botnet. the attacker can use several techniques to scan vulnerable machines. The
attacker first collects Information about a large number of vulnerable machines to create a list.
Subsequently, they infect the machines. The list Is divided by assigning half of the list to the
newly compromised machines. The scanning process runs simultaneously. This technique
ensures the spreading and installation of malicious code in little time.
Which technique is discussed here?
A. Hit-list-scanning technique
B. Topological scanning technique
C. Subnet scanning technique
D. Permutation scanning technique
Answer: (SHOW ANSWER)
One of the biggest problems a worm faces in achieving a very fast rate of infection is "getting off
the ground." although a worm spreads exponentially throughout the early stages of infection, the
time needed to infect say the first 10,000 hosts dominates the infection time.
There is a straightforward way for an active worm a simple this obstacle, that we term hit-list
scanning. Before the worm is free, the worm author collects a listing of say ten,000 to 50,000
potentially vulnerable machines, ideally ones with sensible network connections. The worm, when
released onto an initial machine on this hit-list, begins scanning down the list. once it infects a
machine, it divides the hit-list in half, communicating half to the recipient worm, keeping the other
half.
This fast division ensures that even if only 10-20% of the machines on the hit-list are actually
vulnerable, an active worm can quickly bear the hit-list and establish itself on all vulnerable
machines in only some seconds. though the hit-list could begin at 200 kilobytes, it quickly shrinks
to nothing during the partitioning. This provides a great benefit in constructing a quick worm by
speeding the initial infection.
The hit-list needn't be perfect: a simple list of machines running a selected server sort could
serve, though larger accuracy can improve the unfold. The hit-list itself is generated victimization
one or many of the following techniques, ready well before, typically with very little concern of
detection.
Stealthy scans. Portscans are so common and then wide ignored that even a quick scan of the
whole net would be unlikely to attract law enforcement attention or over gentle comment within
the incident response community. However, for attackers wish to be particularly careful, a
randomised sneaky scan taking many months would be not possible to attract much attention, as
most intrusion detection systems are not currently capable of detecting such low-profile scans.
Some portion of the scan would be out of date by the time it had been used, however abundant of
it'd not.
Distributed scanning. an assailant might scan the web using a few dozen to some thousand
already-compromised "zombies," the same as what DDOS attackers assemble in a very fairly
routine fashion. Such distributed scanning has already been seen within the wild-Lawrence
Berkeley National Laboratory received ten throughout the past year.
DNS searches. Assemble a list of domains (for example, by using wide offered spam mail lists, or
trolling the address registries). The DNS will then be searched for the science addresses of mailservers
(via mx records) or net servers (by looking for www.domain.com).
Spiders. For net server worms (like Code Red), use Web-crawling techniques the same as search
engines so as to produce a list of most Internet-connected web sites. this would be unlikely to
draw in serious attention.
Public surveys. for many potential targets there may be surveys available listing them, like the
Netcraft survey.
Just listen. Some applications, like peer-to-peer networks, wind up advertising many of their
servers. Similarly, many previous worms effectively broadcast that the infected machine is
vulnerable to further attack. easy, because of its widespread scanning, during the Code Red I
infection it was easy to select up the addresses of upwards of 300,000 vulnerable IIS serversbecause
each came knock on everyone's door!
NEW QUESTION: 8
in this form of encryption algorithm, every Individual block contains 64-bit data, and three keys are
used, where each key consists of 56 bits. Which is this encryption algorithm?
A. IDEA
B. Triple Data Encryption standard
C. MDS encryption algorithm
D. AES
Answer: (SHOW ANSWER)
Triple DES is another mode of DES operation. It takes three 64-bit keys, for an overall key length
of 192 bits. In Stealth, you merely type within the entire 192-bit (24 character) key instead of
entering each of the three keys individually. The Triple DES DLL then breaks the user-provided
key into three subkeys, padding the keys if necessary in order that they are each 64 bits long.
The procedure for encryption is strictly an equivalent as regular DES, but it's repeated 3 times ,
hence the name Triple DES. the info is encrypted with the primary key, decrypted with the second
key, and eventually encrypted again with the third key. Triple DES runs 3 times slower than DES,
but is far safer if used properly. The procedure for decrypting something is that the same because
the procedure for encryption, except it's executed in reverse. Like DES, data is encrypted and
decrypted in 64-bit chunks. Although the input key for DES is 64 bits long, the particular key
employed by DES is merely 56 bits long . the smallest amount significant (right-most) bit in each
byte may be a parity , and will be set in order that there are always an odd number of 1s in every
byte. These parity bits are ignored, so only the seven most vital bits of every byte are used,
leading to a key length of 56 bits. this suggests that the effective key strength for Triple DES is
really 168 bits because each of the three keys contains 8 parity bits that aren't used during the
encryption process. Triple DES Modes Triple ECB (Electronic Code Book) * This variant of Triple
DES works precisely the same way because the ECB mode of DES. * this is often the foremost
commonly used mode of operation. Triple CBC (Cipher Block Chaining) * This method is
extremely almost like the quality DES CBC mode. * like Triple ECB, the effective key length is 168
bits and keys are utilized in an equivalent manner, as described above, but the chaining features
of CBC mode also are employed. * the primary 64-bit key acts because the Initialization Vector to
DES. * Triple ECB is then executed for one 64-bit block of plaintext. * The resulting ciphertext is
then XORed with subsequent plaintext block to be encrypted, and therefore the procedure is
repeated. * This method adds an additional layer of security to Triple DES and is therefore safer
than Triple ECB, although it's not used as widely as Triple ECB.
NEW QUESTION: 9
Shiela is an information security analyst working at HiTech Security Solutions. She is performing
service version discovery using Nmap to obtain information about the running services and their
versions on a target system.
Which of the following Nmap options must she use to perform service version discovery on the
target host?
A. -SX
B. -SN
C. -sV
D. -SF
Answer: (SHOW ANSWER)
NEW QUESTION: 10
A. You should use netstat to check for any suspicious connections with another IP address within
the LAN.
B. You should check your ARP table and see if there is one IP address with two different MAC
addresses.
C. You should scan the network using Nmap to check the MAC addresses of all the hosts and
look for duplicates.
D. You cannot identify such an attack and must use a VPN to protect your traffic, r
Answer: (SHOW ANSWER)
NEW QUESTION: 11
The network administrator at Spears Technology, Inc has configured the default gateway Cisco
router's access-list as below:
You are hired to conduct security testing on their network.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list configured at the router prevents you from establishing a successful connection.
You want to retrieve the Cisco configuration from the router. How would you proceed?
A. Use the Cisco's TFTP default password to connect and download the configuration file
B. Run a network sniffer and capture the returned traffic with the configuration file from the router
C. Run Generic Routing Encapsulation (GRE) tunneling protocol from your computer to the router
masking your IP address
D. Send a customized SNMP set request with a spoofed source IP address in the range
-192.168.1.0
Answer: (SHOW ANSWER)
NEW QUESTION: 12
The Payment Card Industry Data Security Standard (PCI DSS) contains six different categories of
control objectives. Each objective contains one or more requirements, which must be followed in
order to achieve compliance. Which of the following requirements would best fit under the
objective, "Implement strong access control measures"?
A. Regularly test security systems and processes.
B. Assign a unique ID to each person with computer access.
C. Use and regularly update anti-virus software on all systems commonly affected by malware.
D. Encrypt transmission of cardholder data across open, public networks.
Answer: (SHOW ANSWER)
NEW QUESTION: 13
Windows LAN Manager (LM) hashes are known to be weak.
Which of the following are known weaknesses of LM? (Choose three.)
A. Makes use of only 32-bit encryption.
B. Hashes are sent in clear text over the network.
C. Effective length is 7 characters.
D. Converts passwords to uppercase.
Answer: (SHOW ANSWER)
NEW QUESTION: 14
Steve, a scientist who works in a governmental security agency, developed a technological
solution to identify people based on walking patterns and implemented this approach to a physical
control access.
A camera captures people walking and identifies the individuals using Steve's approach.
After that, people must approximate their RFID badges. Both the identifications are required to
open the door. In this case, we can say:
A. Although the approach has two phases, it actually implements just one authentication factor
B. Biological motion cannot be used to identify people
C. The solution implements the two authentication factors: physical object and physical
characteristic
D. The solution will have a high level of false positives
Answer: (SHOW ANSWER)
NEW QUESTION: 15
In the field of cryptanalysis, what is meant by a "rubber-hose" attack?
A. Forcing the targeted keystream through a hardware-accelerated device such as an ASIC.
B. A backdoor placed into a cryptographic algorithm by its creator.
C. Extraction of cryptographic secrets through coercion or torture.
D. Attempting to decrypt ciphertext by making logical assumptions about the contents of the
original plaintext.
Answer: (SHOW ANSWER)
A powerful and often the most effective cryptanalysis method in which the attack is directed at the
most vulnerable link in the cryptosystem - the person. In this attack, the cryptanalyst uses
blackmail, threats, torture, extortion, bribery, etc. This method's main advantage is the decryption
time's fundamental independence from the volume of secret information, the length of the key,
and the cipher's mathematical strength.
The method can reduce the time to guess a password, for example, for AES, to an acceptable
level; however, it requires special authorization from the relevant regulatory authorities.
Therefore, it is outside the scope of this course and is not considered in its practical part.
NEW QUESTION: 16
What would you enter if you wanted to perform a stealth scan using Nmap?
A. nmap -sT
B. nmap -sU
C. nmap -sS
D. nmap -sM
Answer: (SHOW ANSWER)
Valid 312-50v12 Dumps shared by PassTestKing.com for Helping Passing 312-50v12 Exam!
PassTestKing.com now offer the newest 312-50v12 exam dumps, the PassTestKing.com
312-50v12 exam questions have been updated and answers have been corrected get the
newest PassTestKing.com 312-50v12 dumps with Test Engine here:
https://www.passtestking.com/ECCouncil/312-50v12-practice-exam-dumps.html (505 Q&As
Dumps, 35%OFF Special Discount Code: freecram)
NEW QUESTION: 17
The Heartbleed bug was discovered in 2014 and is widely referred to under MITRE's Common
Vulnerabilities and Exposures (CVE) as CVE-2014-0160. This bug affects the OpenSSL
implementation of the Transport Layer Security (TLS) protocols defined in RFC6520.
What type of key does this bug leave exposed to the Internet making exploitation of any
compromised system very easy?
A. Public
B. Root
C. Shared
D. Private
Answer: (SHOW ANSWER)
NEW QUESTION: 18
When a normal TCP connection starts, a destination host receives a SYN (synchronize/start)
packet from a source host and sends back a SYN/ACK (synchronize acknowledge). The
destination host must then hear an ACK (acknowledge) of the SYN/ACK before the connection is
established. This is referred to as the "TCP three-way handshake." While waiting for the ACK to
the SYN ACK, a connection queue of finite size on the destination host keeps track of
connections waiting to be completed. This queue typically empties quickly since the ACK is
expected to arrive a few milliseconds after the SYN ACK.
How would an attacker exploit this design by launching TCP SYN attack?
A. Attacker generates TCP ACK packets with random source addresses towards a victim host
B. Attacker generates TCP RST packets with random source addresses towards a victim host
C. Attacker floods TCP SYN packets with random source addresses towards a victim host
D. Attacker generates TCP SYN packets with random destination addresses towards a victim
host
Answer: C (LEAVE A REPLY)
NEW QUESTION: 19
How does a denial-of-service attack work?
A. A hacker prevents a legitimate user (or group of users) from accessing a service
B. A hacker tries to decipher a password by using a system, which subsequently crashes the
network
C. A hacker attempts to imitate a legitimate user by confusing a computer or even another person
D. A hacker uses every character, word, or letter he or she can think of to defeat authentication
Answer: (SHOW ANSWER)
NEW QUESTION: 20
A. WHOIS
B. IETF
C. CAPTCHA
D. IANA
Answer: (SHOW ANSWER)
NEW QUESTION: 21
Which of the following are well known password-cracking programs?
A. Netbus
B. NetCat
C. John the Ripper
D. L0phtcrack
E. Jack the Ripper
Answer: (SHOW ANSWER)
NEW QUESTION: 22
Which of the following is not a Bluetooth attack?
A. Bluedriving
B. Bluesmacking
C. Bluejacking
D. Bluesnarfing
Answer: (SHOW ANSWER)
GitHub - verovaleros/bluedriving: Bluetooth wardriving utility
Bluetooth wardriving utility. Contribute to verovaleros/bluedriving development by creating an account on GitHub.
Bluedriving is a bluetooth wardriving utility. It can capture bluetooth devices, lookup their services,
get GPS information and present everything in a nice web page. It can search for and show a lot
of information about the device, the GPS address and the historic location of devices on a map.
The main motivation of this tool is to research about the targeted surveillance of people by means
of its cellular phone or car. With this tool you can capture information about bluetooth devices and
show, on a map, the points where you have seen the same device in the past.
NEW QUESTION: 23
Which tool can be used to silently copy files from USB devices?
A. USB Snoopy
B. USB Sniffer
C. Use Dumper
D. USB Grabber
Answer: C (LEAVE A REPLY)
NEW QUESTION: 24
While using your bank's online servicing you notice the following string in the URL bar:
"http: // www. MyPersonalBank. com/ account?
id=368940911028389&Damount=10980&Camount=21" You observe that if you modify the
Damount & Camount values and submit the request, that data on the web page reflects the
changes.
Which type of vulnerability is present on this site?
A. XSS Reflection
B. Cookie Tampering
C. Web Parameter Tampering
D. SQL Injection
Answer: (SHOW ANSWER)
NEW QUESTION: 25
Peter, a system administrator working at a reputed IT firm, decided to work from his home and
login remotely. Later, he anticipated that the remote connection could be exposed to session
hijacking. To curb this possibility, he implemented a technique that creates a safe and encrypted
tunnel over a public network to securely send and receive sensitive information and prevent
hackers from decrypting the data flow between the endpoints. What is the technique followed by
Peter to send files securely through a remote connection?
A. SMB signing
B. VPN
C. DMZ
D. Switch network
Answer: (SHOW ANSWER)
NEW QUESTION: 26
Mirai malware targets loT devices. After infiltration, it uses them to propagate and create botnets
that then used to launch which types of attack?
A. Password attack
B. DDoS attack
C. MITM attack
D. Birthday attack
Answer: (SHOW ANSWER)
NEW QUESTION: 27
Todd has been asked by the security officer to purchase a counter-based authentication system.
Which of the following best describes this type of system?
A. An authentication system that creates one-time passwords that are encrypted with secret keys.
B. An authentication system that uses passphrases that are converted into virtual passwords.
C. A biometric system that bases authentication decisions on behavioral attributes.
D. A biometric system that bases authentication decisions on physical attributes.
Answer: (SHOW ANSWER)
NEW QUESTION: 28
Shellshock allowed an unauthorized user to gain access to a server. It affected many Internetfacing
services, which OS did it not directly affect?
A. Linux
B. Unix
C. Windows
D. OS X
Answer: (SHOW ANSWER)
NEW QUESTION: 29
Calvin, a software developer, uses a feature that helps him auto-generate the content of a web
page without manual involvement and is integrated with SSI directives. This leads to a
vulnerability in the developed web application as this feature accepts remote user inputs and uses
them on the page. Hackers can exploit this feature and pass malicious SSI directives as input
values to perform malicious activities such as modifying and erasing server files. What is the type
of injection attack Calvin's web application is susceptible to?
A. CRLF injection
B. Server-side JS injection
C. Server-side includes injection
D. Server-side template injection
Answer: (SHOW ANSWER)
NEW QUESTION: 30
A. Brute Force Attack
B. Online Attack
C. Dictionary Attack
D. Hybrid Attack
Answer: (SHOW ANSWER)
NEW QUESTION: 31
Although FTP traffic is not encrypted by default, which layer 3 protocol would allow for end-to-end
encryption of the connection?
A. SFTP
B. Ipsec
C. SSL
D. FTPS
Answer: (SHOW ANSWER)
IPsec - Wikipedia
Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and
encrypts the packets of data to provide secure encrypted communication between two computers
over an Internet Protocol network. It is used in virtual private networks (VPNs).
IPsec includes protocols for establishing mutual authentication between agents at the beginning
of a session and negotiation of cryptographic keys to use during the session. IPsec can protect
data flows between a pair of hosts (host-to-host), between a pair of security gateways (networkto-
network), or between a security gateway and a host (network-to-host). IPsec uses
cryptographic security services to protect communications over Internet Protocol (IP) networks. It
supports network-level peer authentication, data-origin authentication, data integrity, data
confidentiality (encryption), and replay protection.
The initial IPv4 suite was developed with few security provisions. As a part of the IPv4
enhancement, IPsec is a layer 3 OSI model or internet layer end-to-end security scheme. In
contrast, while some other Internet security systems in widespread use operate above layer 3,
such as Transport Layer Security (TLS) that operates at the Transport Layer and Secure Shell
(SSH) that operates at the Application layer, IPsec can automatically secure applications at the IP
layer.
Incorrect answers:
SFTP https://en.wikipedia.org/wiki/File_Transfer_Protocol#FTP_over_SSH
FTP over SSH is the practice of tunneling a normal FTP session over a Secure Shell connection.
[27] Because FTP uses multiple TCP connections (unusual for a TCP/IP protocol that is still in
use), it is particularly difficult to tunnel over SSH. With many SSH clients, attempting to set up a
tunnel for the control channel (the initial client-to-server connection on port 21) will protect only
that channel; when data is transferred, the FTP software at either end sets up new TCP
connections (data channels) and thus have no confidentiality or integrity protection.
FTPS https://en.wikipedia.org/wiki/FTPS
FTPS (also known FTP-SSL, and FTP Secure) is an extension to the commonly used File
Transfer Protocol (FTP) that adds support for the Transport Layer Security (TLS) and, formerly,
the Secure Sockets Layer cryptographic protocols.
SSL https://en.wikipedia.org/wiki/Transport_Layer_Security
Transport Layer Security (TLS), and its now-deprecated predecessor, Secure Sockets Layer
(SSL), are cryptographic protocols designed to provide communications security over a computer
network. Several versions of the protocols are widely used in applications such as web browsing,
email, instant messaging, and voice over IP (VoIP). Websites can use TLS to secure all
communications between their servers and web browsers.
NOTE: All of these protocols are the application layer of the OSI model.
Valid 312-50v12 Dumps shared by PassTestKing.com for Helping Passing 312-50v12 Exam!
PassTestKing.com now offer the newest 312-50v12 exam dumps, the PassTestKing.com
312-50v12 exam questions have been updated and answers have been corrected get the
newest PassTestKing.com 312-50v12 dumps with Test Engine here:
https://www.passtestking.com/ECCouncil/312-50v12-practice-exam-dumps.html (505 Q&As
Dumps, 35%OFF Special Discount Code: freecram)
NEW QUESTION: 32
which of the following Bluetooth hacking techniques refers to the theft of information from a
wireless device through Bluetooth?
A. Bluesmacking
B. Bluebugging
C. Bluejacking
D. Bluesnarfing
Answer: (SHOW ANSWER)
Bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth
connection, often between phones, desktops, laptops, and PDAs (personal digital assistant).
NEW QUESTION: 33
A zone file consists of which of the following Resource Records (RRs)?
A. SOA, NS, A, and MX records
B. SOA, NS, AXFR, and MX records
C. DNS, NS, PTR, and MX records
D. DNS, NS, AXFR, and MX records
Answer: (SHOW ANSWER)
NEW QUESTION: 34
Which of the following commands checks for valid users on an SMTP server?
A. RCPT
B. CHK
C. VRFY
D. EXPN
Answer: C (LEAVE A REPLY)
The VRFY commands enables SMTP clients to send an invitation to an SMTP server to verify
that mail for a selected user name resides on the server. The VRFY command is defined in RFC
821. The server sends a response indicating whether the user is local or not, whether mail are
going to be forwarded, and so on. A response of 250 indicates that the user name is local; a
response of 251 indicates that the user name isn't local, but the server can forward the message.
The server response includes the mailbox name.
NEW QUESTION: 35
Which iOS jailbreaking technique patches the kernel during the device boot so that it becomes
jailbroken after each successive reboot?
A. Tethered jailbreaking
B. Semi-tethered jailbreaking
C. Untethered jailbreaking
D. Semi-Untethered jailbreaking
Answer: (SHOW ANSWER)
An untethered jailbreak is one that allows a telephone to finish a boot cycle when being pwned
with none interruption to jailbreak-oriented practicality.
Untethered jailbreaks area unit the foremost sought-after of all, however they're additionally the
foremost difficult to attain due to the powerful exploits and organic process talent they need.
associate unbound jailbreak is sent over a physical USB cable association to a laptop or directly
on the device itself by approach of associate application-based exploit, like a web site in
campaign.
Upon running associate unbound jailbreak, you'll be able to flip your pwned telephone off and on
once more while not running the jailbreak tool once more. all of your jailbreak tweaks and apps
would then continue in operation with none user intervention necessary.
It's been an extended time since IOS has gotten the unbound jailbreak treatment. the foremost
recent example was the computer-based Pangu break, that supported most handsets that ran
IOS nine.1. We've additionally witnessed associate unbound jailbreak within the kind of
JailbreakMe, that allowed users to pwn their handsets directly from the mobile campaign
applications programme while not a laptop.
NEW QUESTION: 36
A newly joined employee. Janet, has been allocated an existing system used by a previous
employee. Before issuing the system to Janet, it was assessed by Martin, the administrator.
Martin found that there were possibilities of compromise through user directories, registries, and
other system parameters. He also Identified vulnerabilities such as native configuration tables,
incorrect registry or file permissions, and software configuration errors. What is the type of
vulnerability assessment performed by Martin?
A. Credentialed assessment
B. Database assessment
C. Host-based assessment
D. Distributed assessment
Answer: (SHOW ANSWER)
The host-based vulnerability assessment (VA) resolution arose from the auditors' got to
periodically review systems. Arising before the net becoming common, these tools typically take
an "administrator's eye" read of the setting by evaluating all of the knowledge that an
administrator has at his or her disposal.
Uses
Host VA tools verify system configuration, user directories, file systems, registry settings, and all
forms of other info on a number to gain information about it. Then, it evaluates the chance of
compromise. it should also live compliance to a predefined company policy so as to satisfy an
annual audit. With administrator access, the scans area unit less possible to disrupt traditional
operations since the computer code has the access it has to see into the complete configuration
of the system.
What it Measures Host
VA tools will examine the native configuration tables and registries to spot not solely apparent
vulnerabilities, however additionally "dormant" vulnerabilities - those weak or misconfigured
systems and settings which will be exploited when an initial entry into the setting. Host VA
solutions will assess the safety settings of a user account table; the access management lists
related to sensitive files or data; and specific levels of trust applied to other systems. The host VA
resolution will a lot of accurately verify the extent of the danger by determinant however way any
specific exploit could also be ready to get.
NEW QUESTION: 37
Andrew is an Ethical Hacker who was assigned the task of discovering all the active devices
hidden by a restrictive firewall in the IPv4 range in a given target network.
Which of the following host discovery techniques must he use to perform the given task?
A. UDP scan
B. TCP Maimon scan
C. arp ping scan
D. ACK flag probe scan
Answer: (SHOW ANSWER)
One of the most common Nmap usage scenarios is scanning an Ethernet LAN. Most LANs,
especially those that use the private address range granted by RFC 1918, do not always use the
overwhelming majority of IP addresses. When Nmap attempts to send a raw IP packet, such as
an ICMP echo request, the OS must determine a destination hardware (ARP) address, such as
the target IP, so that the Ethernet frame can be properly addressed. .. This is required to issue a
series of ARP requests. This is best illustrated by an example where a ping scan is attempted
against an Area Ethernet host. The -send-ip option tells Nmap to send IP-level packets (rather
than raw Ethernet), even on area networks. The Wireshark output of the three ARP requests and
their timing have been pasted into the session.
Raw IP ping scan example for offline targets
This example took quite a couple of seconds to finish because the (Linux) OS sent three ARP
requests at 1 second intervals before abandoning the host. Waiting for a few seconds is
excessive, as long as the ARP response usually arrives within a few milliseconds. Reducing this
timeout period is not a priority for OS vendors, as the overwhelming majority of packets are sent
to the host that actually exists. Nmap, on the other hand, needs to send packets to 16 million IP s
given a target like 10.0.0.0/8. Many targets are pinged in parallel, but waiting 2 seconds each is
very delayed.
There is another problem with raw IP ping scans on the LAN. If the destination host turns out to
be unresponsive, as in the previous example, the source host usually adds an incomplete entry
for that destination IP to the kernel ARP table. ARP tablespaces are finite and some operating
systems become unresponsive when full. If Nmap is used in rawIP mode (-send-ip), Nmap may
have to wait a few minutes for the ARP cache entry to expire before continuing host discovery.
ARP scans solve both problems by giving Nmap the highest priority. Nmap issues raw ARP
requests and handles retransmissions and timeout periods in its sole discretion. The system ARP
cache is bypassed. The example shows the difference. This ARP scan takes just over a tenth of
the time it takes for an equivalent IP.
Example b ARP ping scan of offline target
In example b, neither the -PR option nor the -send-eth option has any effect. This is often
because ARP has a default scan type on the Area Ethernet network when scanning Ethernet
hosts that Nmap discovers. This includes traditional wired Ethernet as 802.11 wireless networks.
As mentioned above, ARP scanning is not only more efficient, but also more accurate. Hosts
frequently block IP-based ping packets, but usually cannot block ARP requests or responses and
communicate over the network.Nmap uses ARP instead of all targets on equivalent targets, even
if different ping types (such as -PE and -PS) are specified. LAN.. If you do not need to attempt an
ARP scan at all, specify -send-ip as shown in Example a "Raw IP Ping Scan for Offline Targets".
If you give Nmap control to send raw Ethernet frames, Nmap can also adjust the source MAC
address. If you have the only PowerBook in your security conference room and a large ARP scan
is initiated from an Apple-registered MAC address, your head may turn to you. Use the -spoofmac
option to spoof the MAC address as described in the MAC Address Spoofing section.
NEW QUESTION: 38
What port number is used by LDAP protocol?
A. 445
B. 110
C. 389
D. 464
Answer: (SHOW ANSWER)
NEW QUESTION: 39
Matthew, a black hat, has managed to open a meterpreter session to one of the kiosk machines
in Evil Corp's lobby. He checks his current SID, which is
S-1-5-21-1223352397-1872883824-861252104-501. What needs to happen before Matthew has
full administrator access?
A. He already has admin privileges, as shown by the "501" at the end of the SID.
B. He needs to gain physical access.
C. He needs to disable antivirus protection.
D. He must perform privilege escalation.
Answer: (SHOW ANSWER)
NEW QUESTION: 40
A. SYN
B. RST
C. ACK
D. No return response
Answer: (SHOW ANSWER)
NEW QUESTION: 41
Sam is a penetration tester hired by Inception Tech, a security organization. He was asked to
perform port scanning on a target host in the network. While performing the given task, Sam
sends FIN/ACK probes and determines that an RST packet is sent in response by the target host,
indicating that the port is closed.
What is the port scanning technique used by Sam to discover open ports?
A. Xmas scan
B. IDLE/IPID header scan
C. TCP Maimon scan
D. ACK flag probe scan
Answer: (SHOW ANSWER)
TCP Maimon scan
This scan technique is very similar to NULL, FIN, and Xmas scan, but the probe used here is
FIN/ACK. In most cases, to determine if the port is open or closed, the RST packet should be
generated as a response to a probe request. However, in many BSD systems, the port is open if
the packet gets dropped in response to a probe.
How Nmap interprets responses to a Maimon scan probe
Probe Response Assigned State
No response received (even after retransmissions) open|filtered
TCP RST packet closed
ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) filtered
NEW QUESTION: 42
which of the following information security controls creates an appealing isolated environment for
hackers to prevent them from compromising critical targets while simultaneously gathering
information about the hacker?
A. intrusion detection system
B. Honeypot
C. Botnet
Answer: (SHOW ANSWER)
D Firewall
Explanation:
A honeypot may be a trap that an IT pro lays for a malicious hacker, hoping that they will interact
with it during a way that gives useful intelligence. It's one among the oldest security measures in
IT, but beware: luring hackers onto your network, even on an isolated system, are often a
dangerous game. honeypot may be a good starting place: "A honeypot may be a computer or
computing system intended to mimic likely targets of cyberattacks." Often a honeypot are going to
be deliberately configured with known vulnerabilities in situation to form a more tempting or
obvious target for attackers. A honeypot won't contain production data or participate in legitimate
traffic on your network - that's how you'll tell anything happening within it's a results of an attack. If
someone's stopping by, they're up to no good. That definition covers a various array of systems,
from bare-bones virtual machines that only offer a couple of vulnerable systems to ornately
constructed fake networks spanning multiple servers. and therefore the goals of these who build
honeypots can vary widely also , starting from defense thorough to academic research.
additionally , there's now an entire marketing category of deception technology that, while not
meeting the strict definition of a honeypot, is certainly within the same family. But we'll get thereto
during a moment. honeypots aim to permit close analysis of how hackers do their dirty work. The
team controlling the honeypot can watch the techniques hackers use to infiltrate systems,
escalate privileges, and otherwise run amok through target networks. These sorts of honeypots
are found out by security companies, academics, and government agencies looking to look at the
threat landscape. Their creators could also be curious about learning what kind of attacks are out
there, getting details on how specific sorts of attacks work, or maybe trying to lure a specific
hackers within the hopes of tracing the attack back to its source. These systems are often inbuilt
fully isolated lab environments, which ensures that any breaches don't end in non-honeypot
machines falling prey to attacks. Production honeypots, on the opposite hand, are usually
deployed in proximity to some organization's production infrastructure, though measures are
taken to isolate it the maximum amount as possible. These honeypots often serve both as bait to
distract hackers who could also be trying to interrupt into that organization's network, keeping
them faraway from valuable data or services; they will also function a canary within the coalpit ,
indicating that attacks are underway and are a minimum of partially succeeding.
NEW QUESTION: 43
Roma is a member of a security team. She was tasked with protecting the internal network of an
organization from imminent threats. To accomplish this task, Roma fed threat intelligence into the
security devices in a digital format to block and identify inbound and outbound malicious traffic
entering the organization's network.
Which type of threat intelligence is used by Roma to secure the internal network?
A. Strategic threat intelligence
B. Tactical threat intelligence
C. Operational threat intelligence
D. Technical threat intelligence
Answer: (SHOW ANSWER)
NEW QUESTION: 44
John wants to send Marie an email that includes sensitive information, and he does not trust the
network that he is connected to. Marie gives him the idea of using PGP. What should John do to
communicate correctly using this type of encryption?
A. Use his own public key to encrypt the message.
B. Use Marie's public key to encrypt the message.
C. Use his own private key to encrypt the message.
D. Use Marie's private key to encrypt the message.
Answer: B (LEAVE A REPLY)
When a user encrypts plaintext with PGP, PGP first compresses the plaintext. The session key
works with a very secure, fast conventional encryption algorithm to encrypt the plaintext; the
result is ciphertext. Once the data is encrypted, the session key is then encrypted to the
recipient's public key
Pretty Good Privacy - Wikipedia
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and
authentication for data communication. PGP is used for signing, encrypting, and decrypting texts,
e-mails, files, directories, and whole disk partitions and to increase the security of e-mail
communications.
PGP encryption uses a serial combination of hashing, data compression, symmetric-key
cryptography, and finally public-key cryptography; each step uses one of several supported
algorithms. Each public key is bound to a username or an e-mail address.

Public-key cryptography - Wikipedia
Public key encryption uses two different keys. One key is used to encrypt the information and the
other is used to decrypt the information. Sometimes this is referred to as asymmetric encryption
because two keys are required to make the system and/or process work securely. One key is
known as the public key and should be shared by the owner with anyone who will be securely
communicating with the key owner. However, the owner's secret key is not to be shared and
considered a private key. If the private key is shared with unauthorized recipients, the encryption
mechanisms protecting the information must be considered compromised.
NEW QUESTION: 45
Sam, a web developer, was instructed to incorporate a hybrid encryption software program into a
web application to secure email messages. Sam used an encryption software, which is a free
implementation of the OpenPGP standard that uses both symmetric-key cryptography and
asymmetric-key cryptography for improved speed and secure key exchange. What is the
encryption software employed by Sam for securing the email messages?
A. GPG
B. SMTP
C. PGP
D. S/MIME
Answer: C (LEAVE A REPLY)
NEW QUESTION: 46
Which of the following is considered an exploit framework and has the ability to perform
automated attacks on services, ports, applications and unpatched security flaws in a computer
system?
A. Wireshark
B. Maltego
C. Metasploit
D. Nessus
Answer: (SHOW ANSWER)

Metasploit - Wikipedia
The Metasploit Project is a computer security project that provides information about security
vulnerabilities and aids in penetration testing and IDS signature development. It is owned by
Boston, Massachusetts-based security company Rapid7.
Its best-known sub-project is the open-source Metasploit Framework, a tool for developing and
executing exploit code against a remote target machine. Other important sub-projects include the
Opcode Database, shellcode archive and related research.
The Metasploit Project includes anti-forensic and evasion tools, some of which are built into the
Metasploit Framework. Metasploit is pre-installed in the Kali Linux operating system.
The basic steps for exploiting a system using the Framework include.
1. Optionally checking whether the intended target system is vulnerable to an exploit.
2. Choosing and configuring an exploit (code that enters a target system by taking advantage of
one of its bugs; about 900 different exploits for Windows, Unix/Linux and macOS systems are
included).
3. Choosing and configuring a payload (code that will be executed on the target system upon
successful entry; for instance, a remote shell or a VNC server). Metasploit often recommends a
payload that should work.
4. Choosing the encoding technique so that hexadecimal opcodes known as "bad characters" are
removed from the payload, these characters will cause the exploit to fail.
5. Executing the exploit.
This modular approach - allowing the combination of any exploit with any payload - is the major
advantage of the Framework. It facilitates the tasks of attackers, exploit writers and payload
writers.
Valid 312-50v12 Dumps shared by PassTestKing.com for Helping Passing 312-50v12 Exam!
PassTestKing.com now offer the newest 312-50v12 exam dumps, the PassTestKing.com
312-50v12 exam questions have been updated and answers have been corrected get the
newest PassTestKing.com 312-50v12 dumps with Test Engine here:
https://www.passtestking.com/ECCouncil/312-50v12-practice-exam-dumps.html (505 Q&As
Dumps, 35%OFF Special Discount Code: freecram)
NEW QUESTION: 47
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that
allows session oriented connections (Telnet) and performs the sequence prediction on the target
operating system. He manages to find an active session due to the high level of traffic on the
network. What is Bob supposed to do next?
A. Guess the sequence numbers
B. Reverse sequence prediction
C. Take over the session
D. Take one of the parties offline
Answer: (SHOW ANSWER)
NEW QUESTION: 48
An attacker runs netcat tool to transfer a secret file between two hosts.
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
A. Use cryptcat instead of netcat
B. Machine A: netcat -l -p 1234 < testfile -pw passwordMachine B: netcat <machine A IP> 1234 -
pw password
C. Machine A: netcat -l -e magickey -p 1234 < testfileMachine B: netcat <machine A IP> 1234
D. Machine A: netcat -l -p -s password 1234 < testfileMachine B: netcat <machine A IP> 1234
Answer: (SHOW ANSWER)
NEW QUESTION: 49
Based on the below log, which of the following sentences are true?
Mar 1, 2016, 7:33:28 AM 10.240.250.23 - 54373 10.249.253.15 - 22 tcp_ip
A. Application is FTP and 10.240.250.23 is the client and 10.249.253.15 is the server.
B. Application is SSH and 10.240.250.23 is the server and 10.249.253.15 is the client.
C. SSH communications are encrypted; it's impossible to know who is the client or the server.
D. Application is SSH and 10.240.250.23 is the client and 10.249.253.15 is the server.
Answer: (SHOW ANSWER)
Mar 1, 2016, 7:33:28 AM 10.240.250.23 - 54373 10.249.253.15 - 22 tcp_ip Let's just disassemble
this entry.
Mar 1, 2016, 7:33:28 AM - time of the request
10.240.250.23 - 54373 - client's IP and port
10.249.253.15 - server IP
- 22 - SSH port
NEW QUESTION: 50
A. sudo tshark -f''net 192 .68.8.0/24''
B. wireshark --capture --local masked 192.168.8.0 ---range 24
C. tshark -net 192.255.255.255 mask 192.168.8.0
D. wireshark --fetch ''192.168.8*''
Answer: (SHOW ANSWER)